- Robocalling, enabled by VoIP, causes real social harm
- Filtering based on Caller ID brings some temporary relief
- The telecom industry has real work ahead to protect Caller ID with STIR
VoIP Drove down the cost of making phone calls. We love that about VoIP: free long distance! In the telecom industry now, the idea that calls within a country would cost a retail user more than local calls seems quaint.
But the low cost of VoIP calling has brought a new adversary: “Robocalling,” so called because “Robots” (computers with pre-recorded messages) place phone calls. Many of these calls are placed in violation of existing laws. According to US Federal Trade Commission official Lois Greisman, lawbreakers “can place robocalls for less than one cent per minute,” and I suspect that only counts the calls that are actually answered. And though the call may be dialed by an automaton, it may be connected to a live person when its answered.
Elderly Victimized by VoIP Robocalling
The main ones who suffer are non-VoIP Users, disproportionately the elderly. Older people see no reason to switch from the same telephone service they’ve had most of their lives, and they retain legacy, POTS-based phone service. In rural areas, this is often served by feature-poor TDM equipment with only “Custom Local Area Signal Services” (CLASS) features, developed in the 1980s in the rotary phone era. The best available Robocall blocking uses Simultaneous Ring, which is not available in the CLASS feature set in classic telephone service.

Because the pain of these automated calls is felt so acutely by elderly citizens in America, the US Senate Special Committee on Aging is pushing for laws to force Service Providers to Provide Blocking. That the Aging Committee is pushing to regulate telephone services serves as evidence of the gravity.
By building efficient networks, VoIP technologists unwittingly created a special problem for users of legacy technology. (Hint: if you have aging relatives, be sure to upgrade their phone service to a modern option.)
“We now have this onslaught—it’s terrible,” said Indiana Attorney General Greg Zoeller, who added that the scams are “primarily directed at seniors.” Scammers attempt to trick seniors into paying for taxes they don’t owe, or providing banking information for lotteries they haven’t won.
The Wall Street Journal reports on one 88-year-old Arkansan who lost $110,932. And often, blocking or changing the Caller ID of the Robocaller is a key part of the scam. Another 57-year-old person lost nearly $250,000 in a scam relying on a “device that conceals the identity and location of the caller.”
The Nature of the Problem
Attackers setu
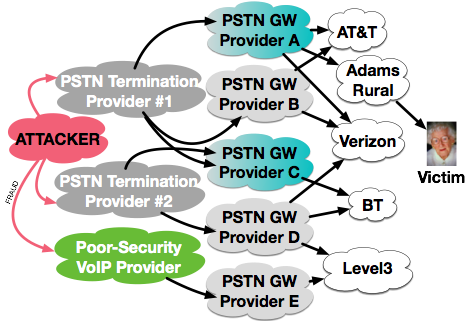 Scammers and other illegal robocallers send calls through multiple networks, sometimes using Least Cost Routing, or stolen phone service.
Scammers and other illegal robocallers send calls through multiple networks, sometimes using Least Cost Routing, or stolen phone service.p computers to launch outbound attacks, undoubtedly through VoIP protocols, and send them through grey-market PSTN Termination Providers. These are firms that offer low rates to accept a SIP telephone call and deliver it to a PSTN phone. But if they do nothing to ensure that the caller IDs used are accurate, and may be respond slowly to complaints against their customers. Further, they may choose to not participate in CDR-based Call Traces, the de facto industry standard method used to determine the source of a call. These can be anywhere in the world, and these firms need not exist for long.
The PSTN Termination Providers typically don’t actually operate PSTN Gateways themselves. That is, they have no ability to directly send the traffic into the legacy TDM SS7/C7 telephone network to reach any phone in the world. So the PSTN Termination Providers buy services from more legitimate PSTN Gateway (PSTN GW) Providers. These PSTN Gateway Providers then have direct connections to the major telephone carriers of the world, and paths to reach all the smaller ones as well.
AT&T is an example of the PSTN Gateway (GW). In an FCC Hearing on Robocalling in September, 2015, Adam Panagia of AT&T reports that they often receive a single coordinated Robocalling campaign through 20 or more wholesale carriers. If even a legitimate call center in India is routing calls the US, AT&T may receive calls from that single call center through 30 to 50 wholesale customers.
VoIP Fraud Plays a Role
In addition to the use of PSTN Termination Providers to perpetrate Robocalling fraud, some attackers use exploited VoIP Telephone Providers. In these cases, a VoIP provider has a security vulnerability, such as a SIP account with a simple password, or a customer device that is not protected by a firewall.
When attackers get access to this service provider, they use it as one of the paths to send calls to the victims. The defrauded Service Providers whose service is stolen are victims along with those who are called and then scammed. The poor security of many VoIP Service Providers contributes to the Robocalling problem, but Service Providers have the power to improve their security.
Solving the Problem Technically
Blocking Historically Disallowed Historically, Telephone Service Providers in the US were prevented from blocking calls sent to a subscriber. If you bought service from one, and had a telephone number, then the Service Provider was obligated to deliver every call. The FCC changed that in June, 2015, in a Declaratory Ruling, and by September of that year they were running workshops to encourage the proper kind of blocking.
The FCC made a welcome change, and though some service providers were already providing some types of blocking before the June 2015 ruling, it opens options for blocking calls even among the scrupulous. So the question is now: which calls should be blocked?
Caller ID Trusted Currently, Caller ID fundamentally trusted from the original caller. Unlike modern email, there is no technical mechanism to confirm that the caller ID provided on a call is actually genuine. VoIP technology, such as SIP From, “Trust Domains” P-Asserted-Identity, and SIP “Identity” have not helped because they only apply to limited areas of the network, and don’t provide any certainty as a call travels from a call center in India to a retiree in Iowa.
Verifiable Caller ID is a key requirement to block scammers, according to Scott Mullen, VP Technology of Bandwidth.com. They're a major PSTN termination and origination firm in the USA with extensive SS7/TDM interconnects, noted in the FCC workshop that toll-free fraud is a major problem they deal with. Even International calls come through in a way that tricks the US recipient into believing it's a call originating from the US.
Problem Calls Distributed Further, calls from scammers are distributed across many networks. One PSTN GW Provider has some data, while another has different data. It’s not easy to coalesce the information into a unified view to make smart decisions about the call.
Can’t scan a phone call before delivery Another difficulty for scanning telephone calls lies in the real-time nature: unlike an email that can be analyzed in its entirety before it is deposited into your mailbox, only a few bits of information are available to a call-blocking system: (a) Time of call, (b) Claimed Calling party number, (c) Called party number, (d) Input source (such as a particular wholesale customer link).
I should note that we can learn about calls after they are delivered: Robocalls that are answered are usually disconnected very quickly. Short call durations provide some clues after some of the calls are delivered, which may be used to improve the go/no-go decision for future calls.
Technology Types Calls do flow across and SIP and TDM networks: but scam calls almost always originate as SIP. The cost of maintaining TDM infrastructure appears to be too high for scammers, as it probably invalidates the business model.
Give me a call, never
For the moment, Call Blocking based on Caller ID reputation is providing some relief. These work by using a database of known scammer caller IDs, then blocking the calls that are in that database.
The industry de facto standard for Personal Blocking Services is NOMOROBO, released in 2013 after winning a US Federal Trade Commission competition for technical solutions to Robocalling. At the September 2015, NOMOROBO was that annoying better sibling, with the FCC mom asking all the other participants, in effect, “Why can’t you be more like NOMOROBO?”
Nomorobo is free, and blocks calls from Caller IDs that are repeatedly used for annoying calls. It’s available to anyone who has Simultaneous Ring, a feature found on Broadworks, Metaswitch, and most other modern telecom platforms.
How Grandma Gets Attacked
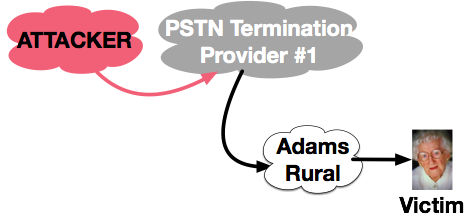 Calls normally route through one or more PSTN Termination Providers before they reach an ordinary telephone company and their victim.
Calls normally route through one or more PSTN Termination Providers before they reach an ordinary telephone company and their victim.Let’s first look at the normal call path from an attacker to the Victim. In this case, we’ll say that the victim is a subscriber of “Adams Rural Telephone Company.” The Attacker launches calls, dialing outbound calls, and some of those calls route to “PSTN Termination Provider #1”. This company determine where the calls should route, and, in those cases where Adams’ subscribers are the victim, routes the calls to Adams’. This supposes that both Adams and the Attacker do business with the same PSTN Termination Provider, but in many cases there will be several intermediate PSTN Providers.
How Grandma Blocks the Attack
NOMOROBO depends on the Simultaneous Ring feature. To use it, Grandma would setup her calls to ring both her phone and the Personal Blocking Service at the same time.
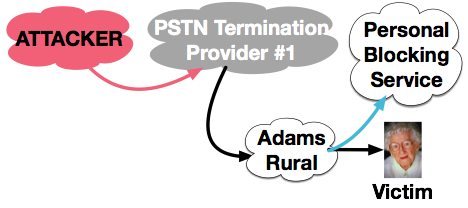 A Personal blocking service, like NOMOROBO, receives the call through Simultaneous Ring / Call Forking setup on the Victim's phone. If the Caller ID is in the blacklist, NOMOROBO answers the call, which prevents the Victim from answering.
A Personal blocking service, like NOMOROBO, receives the call through Simultaneous Ring / Call Forking setup on the Victim's phone. If the Caller ID is in the blacklist, NOMOROBO answers the call, which prevents the Victim from answering.In this way, NOMOROBO receives an inbound call with the Caller ID provided by the Attacker. If NOMOROBO finds this Caller ID in its blacklist database, it can answer the call – thus ending the call for the Victim. The victim experiences only a single telephone ring.
NOMOROBO is clearly a market leader. They are benefiting from the “Network Effect,” where their popularity makes the service work better by aggregating data. NOMOROBO certainly receives many simultaneous calls during Robocall campaigns, and can exploit the concurrency to make smarter decisions.
But NOMOROBO must depend on the caller ID and called ID only, and cannot do anything to improve the quality of the data. NOMOROBO does not know when calls end (i.e., the duration of answered calls), so it cannot improve its decisions based on calls that turn out to be undesirable and are quickly ended.
NOMOROBO also cannot analyze the audio of the phone call. In the US, many Robocalls begin with dead silence, which is unnatural for ordinary person-to-person calls. Normal humans use this to decide which calls to hang up quickly. This mismatch between robocalls and human-dialed calls should be useful to an automated blocking system, if it were available.
Service-Provider Based Blocking
What happens when the victim does not have the Simultaneous Ring service, or lacks the skills to set it up? Or what if a Service Provider would like to block Robocalls for all of its subscribers? Telephone Service Providers can also block calls by using a network-based service.
Consider the network path shown. Normally calls flow from the Attacker, to an intermediate, and finally to the victim’s service provider.
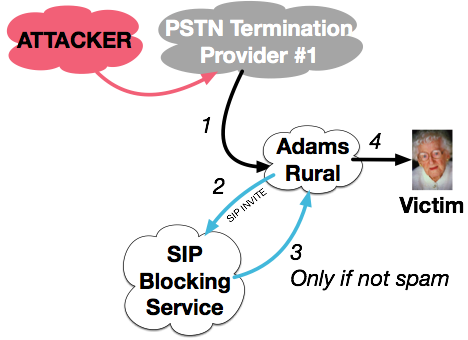 A Service-Provider Based Blocking Service can provide protection for every customer of a service provider. Using SIP, the calls can be routed through an intermediate device that checks the caller ID. Or, potentially, it could analyze the audio or look for other signatures of fraud.
A Service-Provider Based Blocking Service can provide protection for every customer of a service provider. Using SIP, the calls can be routed through an intermediate device that checks the caller ID. Or, potentially, it could analyze the audio or look for other signatures of fraud.Service Providers (SPs) can provide protection by using SIP call routing to route calls through an intermediate service. Instead of immediately sending every call to the victim, the SP can route the call to an intermediate service (or device) that checks the blacklist database. To borrow the term from email, only the calls that are not spam are ultimately delivered to the end user.
The Metaswitch SIP Robocall Blocking Service is a current market example of a service using SIP to address this problem. Service Providers can route their calls to the service, which blocks calls coming from caller ID numbers in the blacklist database.
This network model can provide robocall-blocking for an entire Service Provider, and not just for a single user. It’s also far more efficient than Personal Call Blocking, because it doesn’t require all the setup for a media path through the legacy PSTN to check the database for each call.
It also has opportunities for future development: with a stateful SIP proxy, a SP robocall blocking service could know when calls start and end. And once privacy concerns are handled, this approach analyze the audio for hints, such as dead-silence at the start of a call.
But like Personal Call Blocking, this approach still relies on the caller ID, which can be faked for each call.
Nothing is any good if other people like it
Blacklist based blocking services work today precisely because they are not popular. Today’s blocking services rely on calling party ID, as if that’s trustworthy. Scammers do have some incentive to place calls from the same caller ID repeatedly: once they find a telephone number with a matching CNAM caller name that people will answer – with names like “Internal Rev Service,” or “EDUC LOTTERY” – they seem to stick with that same number.
But Robocallers are already adapting to robocall blocking services. Some are calling from randomly-selected working, legal telephone numbers. This method completely defeats simplistic blacklist databases.
This means we really need a trustworthy caller ID. And some in the industry are working to provide it.
Engineers in the Internet Engineering Task Force (IETF) and the Alliance for Telecommunications Industry Solutions (ATIS) have developed a standard called STIR, “Secure Telephony Identifiers Revisited”. When used as designed, each call using STIR will include a signature as evidence that the calling party has the right to call from the telephone number they’re using.
This would be implemented at the entry to the SIP-PSTN network, ideally at the customer’s PBX or at their first Service Provider Interface. For example, a BroadWorks service provider may use SIP authentication to confirm the identity of a caller, and then create the STIR cryptographic signature to confirm the legitimacy of the caller ID.
Don't strip that header
Currently, there are no SIP headers that must be retained end-to-end through the VoIP networks. All headers can be reconstructed at each step, though a few elements are reused (such as the calling and called party numbers). STIR assumes that VoIP carriers will be able to pass a SIP header through their network from the origin to the terminating carrier. This is certainly technically feasible, but will require substantial coordination – and likely a few SBC software updates for some carriers.
STIR promises a world where you can be certain of the calling party while your phone is ringing. But will it happen? STIR requires substantial technical work on VoIP network infrastructure. Practically every SIP carrier peering/trunk on every SBC deployed will have to be updated.
STIR will require establishment of a Certificate Authority (CA) who can provide the certificates verifying the right to use telephone numbers. We already have Certificate Authorities in the industry servicing the Web industry, so this should not be a major hurdle. You can expect big carriers to desire to be CAs for themselves – likely a smart solution for many cases. For example, AT&T has been, in effect, the “owner” of millions of telephone numbers for years, though they were permaently assigned to their subscribers. It makes sense for AT&T to be the CA for the numbers it already “owns”.
Who Goes There?
To succeed, STIR will have to engage the business models of the modern VoIP PSTN. Private companies and government entities alike use the flexibility of the PSTN to route their calls through any carrier that is convenient. If STIR requires evidence that the telephone number is being used legitimately, then credentials to use the telephone numbers must be distributed to all of the owners of telephone numbers.
Video Relay Service. For example, at the SIP Forum SIPNOC meeting in June 2016, one major Video Relay Service (VRS) for the Deaf and Hard-of-Hearing community commented that they effectively place calls on behalf of their users. A full STIR implementation will require the VRS providers to place the calls outbound for these users, even though the audio portion is actually connected to a Sign-Language Interpreter.
Government Agencies. Government agencies using COTS platforms like BroadWorks sometimes use a variety of paths for routing their calls outbound. They, too, will need the tools and technology to prove their right to use the caller ID, because preventing spoofing of calls from public institutions is one of hopes for STIR.
Call Center Services. Today it’s also common for a firm to hire a call center service to place outbound calls, representing a firm. STIR will require the Call Center firms to be capable of providing a signature showing the right to place calls from that entity. For example, if the Call Center for Delta Airlines needs to call you, then the Call Center service will need credentials (like a password) to allow them to place that outbound call from Delta’s telephone number. The Call Center will need to be upgraded to be capable of generating the STIR Identities.
Ten Years of Work
Once Caller IDs are verifiable, telephone users can make smart decisions about which calls they want to allow.
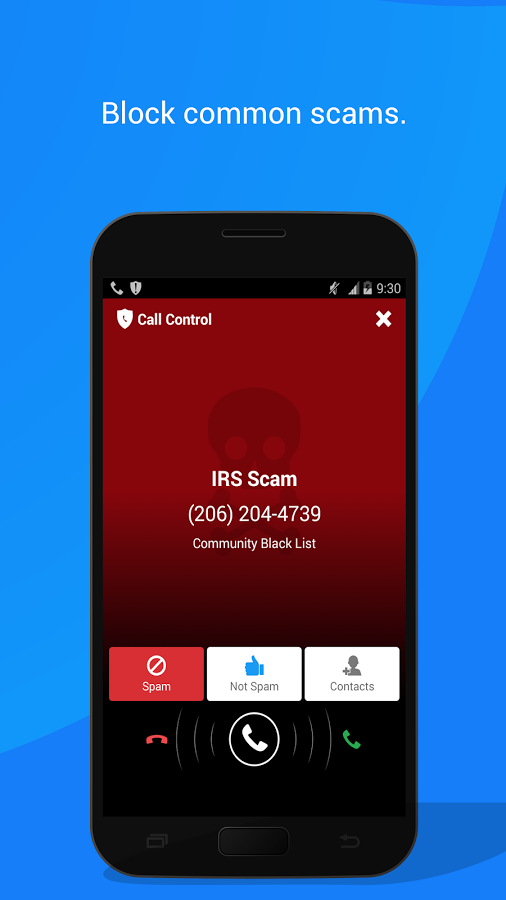 Call Control from Kedlin Company operates on the phone endpoint.
Call Control from Kedlin Company operates on the phone endpoint.So How long will it take to block fraudulent caller ID, and get true caller ID? It took about seven years to prevent spoofing of domain names, like “gmail.com”, from the start of the IESG SPF experiment in 2005 to the implementation of DMARC in 2012. The PSTN moves even slower.
But solving the spoofed-caller-ID problem – and the Robocalling it enables – are worth doing. Service Providers should monitor the progress of STIR, and Vendors (like BroadSoft, Oracle Communications, Metaswitch, Genband, Sonus) should plan to support STIR.
- Push for STIR Identity Support from your SIP Software Vendor, especially SBC, Feature Servers, and SIP Trunking Devices
- Configure your equipment to allow the new Identity header to flow through
- Find out how you can confirm and display the identity of calls you receive using STIR
- Plan to enable users to legitimately delegate authority to place outbound calls
